Cisco® 350-701 Exam Practice Questions (P. 5)
- Full Access (704 questions)
- Six months of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #41
What provides the ability to program and monitor networks from somewhere other than the DNAC GUI?
send
light_mode
delete
Question #42
What is a function of 3DES in reference to cryptography?
- AIt encrypts traffic.
- BIt creates one-time use passwords.
- CIt hashes files.
- DIt generates private keys.
Correct Answer:
A
A
send
light_mode
delete
Question #43
Which two activities can be done using Cisco DNA Center? (Choose two.)
- ADHCP
- BdesignMost Voted
- Caccounting
- DDNS
- EprovisionMost Voted
Correct Answer:
BE
Reference:
https://www.cisco.com/c/en/us/td/docs/cloud-systems-management/network-automation-and-management/dna-center/1-2-1/user_guide/ b_dnac_ug_1_2_1/b_dnac_ug_1_2_chapter_00.pdf
BE
Reference:
https://www.cisco.com/c/en/us/td/docs/cloud-systems-management/network-automation-and-management/dna-center/1-2-1/user_guide/ b_dnac_ug_1_2_1/b_dnac_ug_1_2_chapter_00.pdf
send
light_mode
delete
Question #44
Which PKI enrollment method allows the user to separate authentication and enrollment actions and also provides an option to specify HTTP/TFTP commands to perform file retrieval from the server?
send
light_mode
delete
Question #45
Which type of API is being used when a security application notifies a controller within a software-defined network architecture about a specific security threat?
- Asouthbound API
- Bwestbound API
- Ceastbound API
- Dnorthbound APIMost Voted
Correct Answer:
D
D
send
light_mode
delete
Question #46
An organization has two machines hosting web applications. Machine 1 is vulnerable to SQL injection while machine 2 is vulnerable to buffer overflows. What action would allow the attacker to gain access to machine 1 but not machine 2?
- Asniffing the packets between the two hosts
- Bsending continuous pings
- Coverflowing the buffer's memory
- Dinserting malicious commands into the databaseMost Voted
Correct Answer:
D
D
send
light_mode
delete
Question #47
What is the function of SDN southbound API protocols?
- Ato allow for the static configuration of control plane applications
- Bto enable the controller to use REST
- Cto enable the controller to make changesMost Voted
- Dto allow for the dynamic configuration of control plane applications
Correct Answer:
C
C
send
light_mode
delete
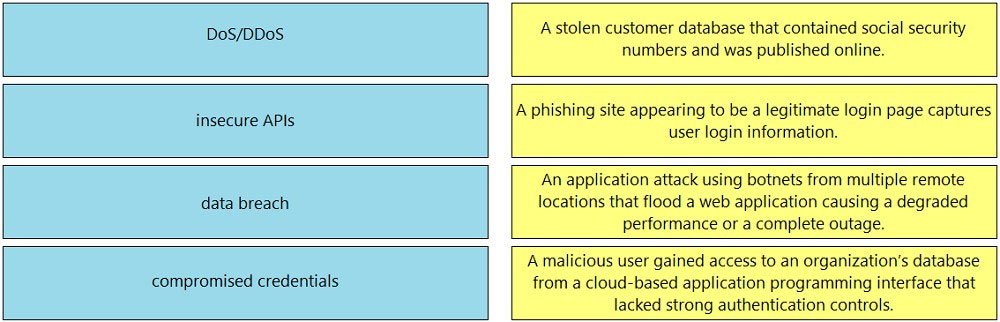
Question #48
DRAG DROP -
Drag and drop the threats from the left onto examples of that threat on the right.
Select and Place:
Drag and drop the threats from the left onto examples of that threat on the right.
Select and Place:

send
light_mode
delete
Question #49
What is the difference between Cross-site Scripting and SQL Injection attacks?
- ACross-site Scripting is when executives in a corporation are attacked, whereas SQL Injection is when a database is manipulated.
- BCross-site Scripting is an attack where code is executed from the server side, whereas SQL Injection is an attack where code is executed from the client side.Most Voted
- CCross-site Scripting is a brute force attack targeting remote sites, whereas SQL Injection is a social engineering attack.
- DCross-site Scripting is an attack where code is injected into a database, whereas SQL Injection is an attack where code is injected into a browser.
Correct Answer:
B
B
send
light_mode
delete
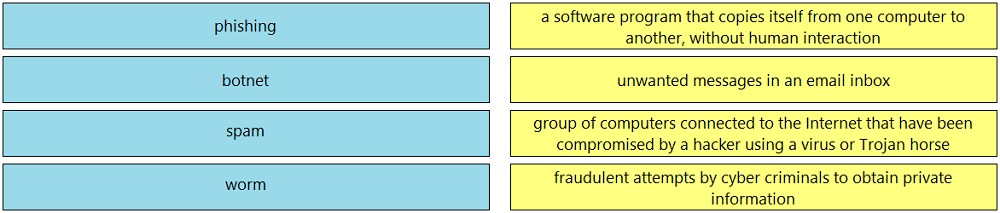
Question #50
DRAG DROP -
Drag and drop the common security threats from the left onto the definitions on the right.
Select and Place:
Drag and drop the common security threats from the left onto the definitions on the right.
Select and Place:

send
light_mode
delete
All Pages