Cisco® 300-210 Exam Practice Questions (P. 5)
- Full Access (563 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #41


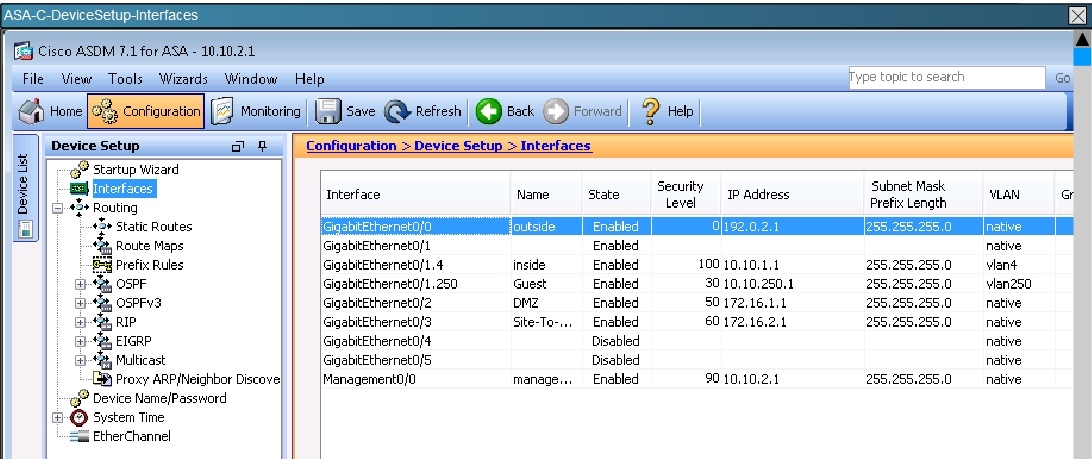

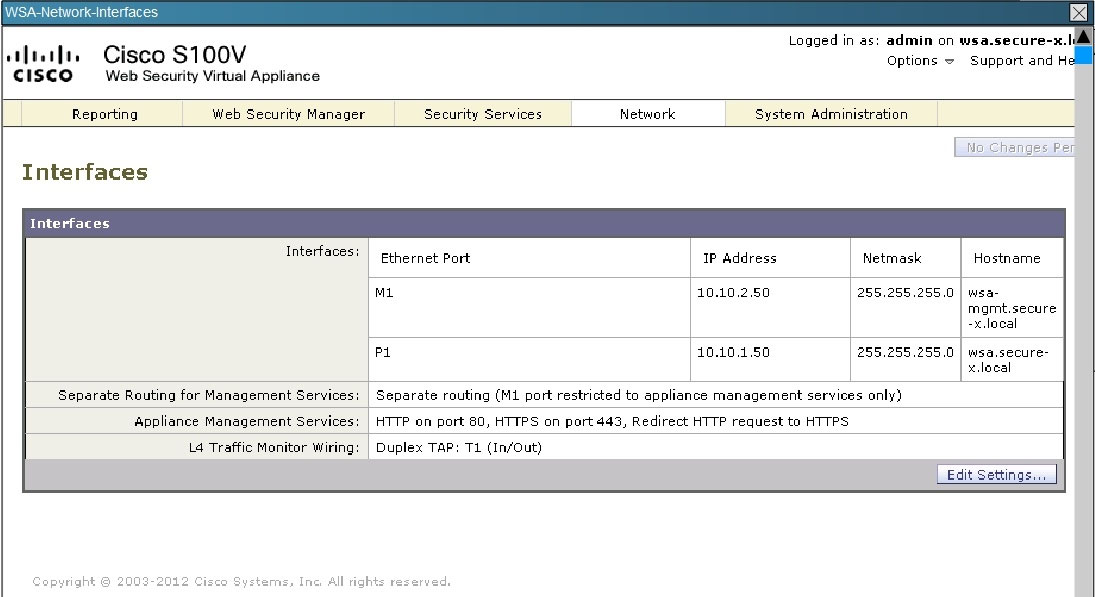
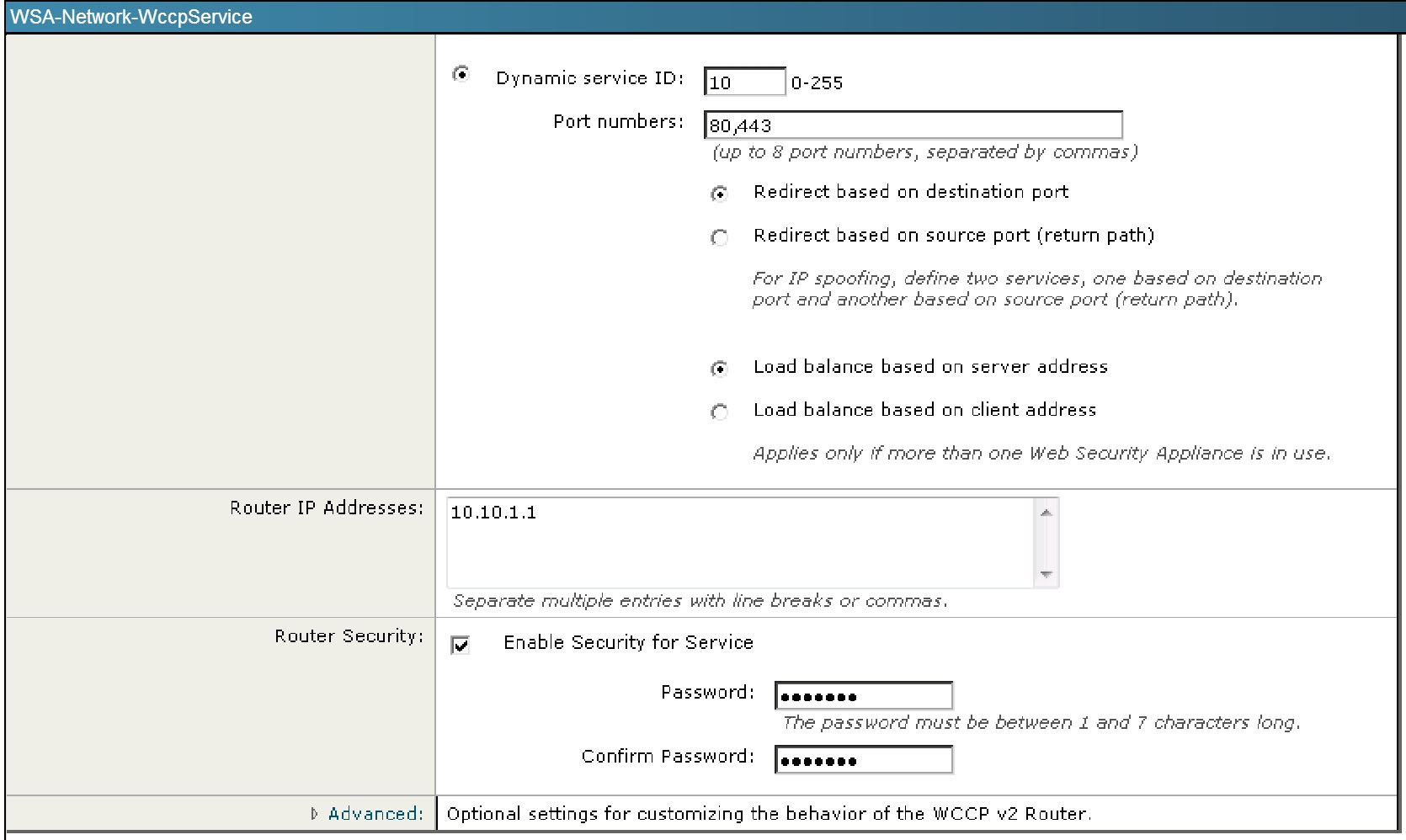
Between the Cisco ASA configuration and the Cisco WSA configuration, what is true with respect to redirected ports?
- ABoth are configured for port 80 only.
- BBoth are configured for port 443 only.
- CBoth are configured for both port 80 and 443.
- DBoth are configured for ports 80, 443 and 3128.
- EThere is a configuration mismatch on redirected ports.
Correct Answer:
C
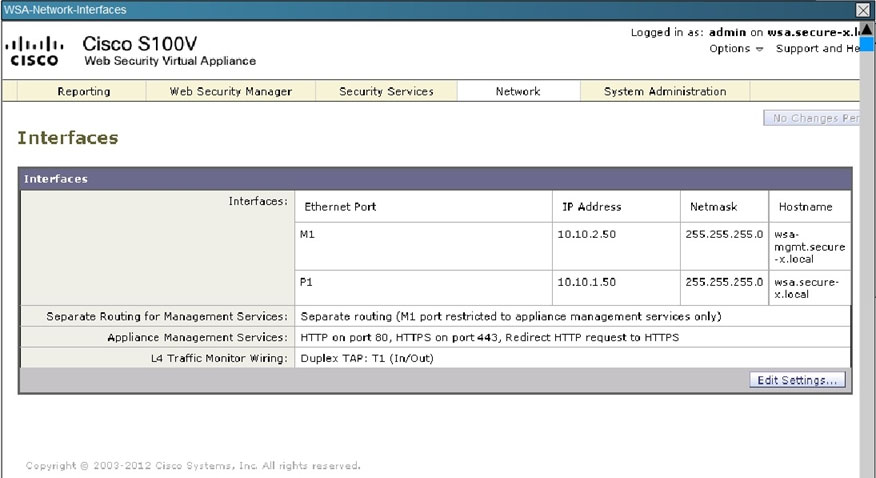
This can be seen from the WSA Network tab shown below:
C
This can be seen from the WSA Network tab shown below:

send
light_mode
delete
Question #42


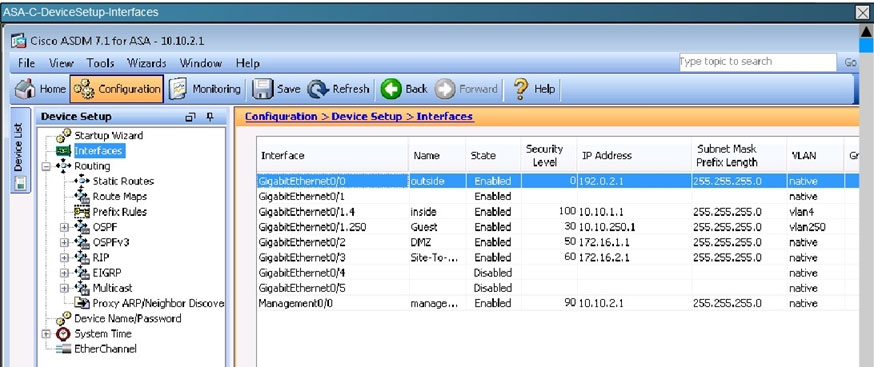
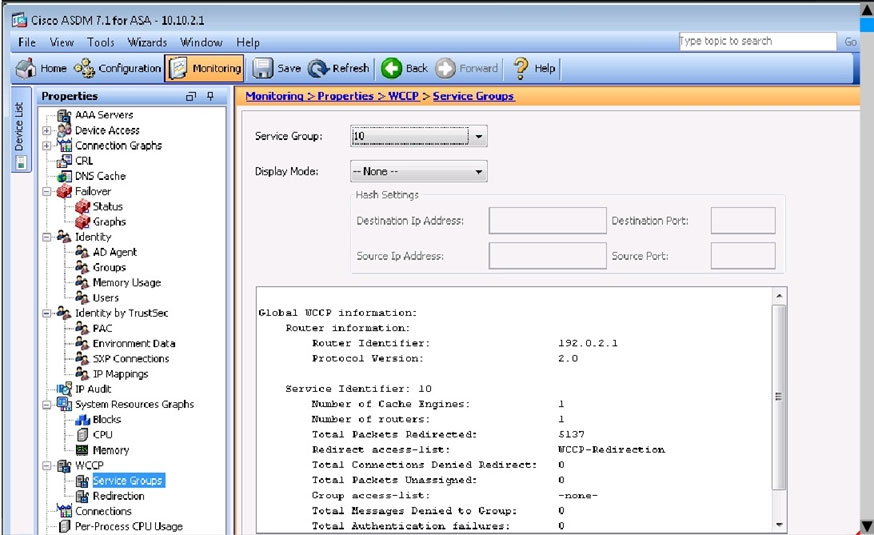
Which of the following is true with respect to the version of WCCP configured on the Cisco ASA and the Cisco WSA?
- ABoth are configured for WCCP v1.
- BBoth are configured for WCCP v2.
- CBoth are configured for WCCP v3.
- DThere is a WCCP version mismatch between the Cisco WSA and the Cisco ASA.
Correct Answer:
B
WCCP version shows as version 2.0:
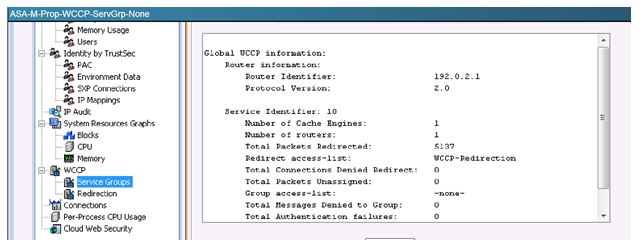
WSA also shows version 2 is being used:
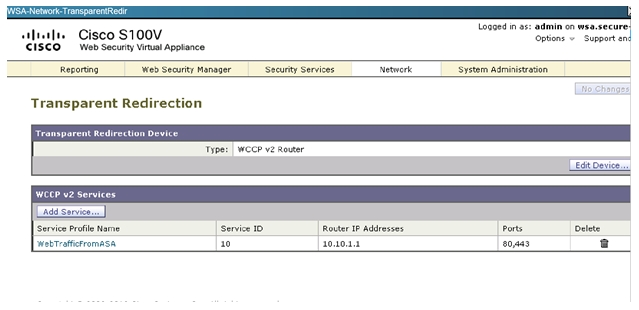
B
WCCP version shows as version 2.0:

WSA also shows version 2 is being used:

send
light_mode
delete
Question #43
When you create a new server profile on the Cisco ESA, which subcommand of the ldapconfig command configures spam quarantine end-user authentication?
send
light_mode
delete
Question #44
What is a value that Cisco ESA can use for tracing mail flow?
- Athe source IP address
- Bthe FQDN of the destination IP address
- Cthe destination IP address
- Dthe FQDN of the source IP address
Correct Answer:
D
D
send
light_mode
delete
Question #45
Which option is a benefit of Cisco Email Security virtual appliance over the Cisco ESA appliance?
- Aglobal threat intelligence updates from Talos
- Breduced space and power requirements
- Coutbound message protection
- Dautomated administration
Correct Answer:
B
B
send
light_mode
delete
Question #46
Which three sender reputation ranges identify the default behavior of the Cisco Email Security Appliance? (Choose three.)
- AIf it is between -10 and -4, the email is blocked
- BIf it is between +1 and +10, the email is accepted
- CIf it is between -10 and -3, the email is blocked
- DIf it is between -10 and -3, the email is sent to the virus and spam engines for additional scanning
- EIf it is between -3 and +1, the email is accepted and additional emails from the sender are throttled
- FIf it is between -1 and +10, the email is accepted
- GIf it is between -3 and -1, the email is accepted and additional emails from the sender are throttled
- HIf it is between -4 and +1, the email is accepted and additional emails from the sender are throttled
Correct Answer:
CFG
CFG
send
light_mode
delete
Question #47
What is the function of the Web Proxy Auto-Discovery protocol?
- AIt enables a web client's traffic flows to be redirected in real time.
- BIt enables web clients to dynamically resolve hostname records.
- CIt enables a web client to download a script or configuration file that is named by a URL.
- DIt enables a web client to discover the URL of a configuration file.
Correct Answer:
D
D
send
light_mode
delete
Question #48
On Cisco Firepower Management Center, which policy is used to collect health modules alerts from managed devices?
- Ahealth policy
- Bsystem policy
- Ccorrelation policy
- Daccess control policy
- Ehealth awareness policy
Correct Answer:
A
A
send
light_mode
delete
Question #49
Which piece of information required to perform a policy trace for the Cisco WSA?
- Athe destination IP address of the trace
- Bthe source IP address of the trace
- Cthe URL to trace
- Dauthentication credentials to make the request
Correct Answer:
C
C
send
light_mode
delete
Question #50
With Cisco FirePOWER Threat Defense software, which interface mode do you configure to passively receive traffic that passes through the appliance?
send
light_mode
delete
All Pages
