Cisco® 210-250 Exam Practice Questions (P. 4)
- Full Access (1130 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #31
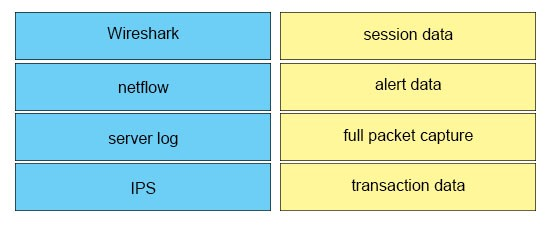
DRAG DROP -
Drag the data source on the left to the correct data type on the right.
Select and Place:
Drag the data source on the left to the correct data type on the right.
Select and Place:
send
light_mode
delete
Question #32
Which protocol maps IP network addresses to MAC hardware addresses so that IP packets can be sent across networks?
- AInternet Control Message Protocol
- BAddress Resolution Protocol
- CSession Initiation Protocol
- DTransmission Control Protocol/Internet Protocol
Correct Answer:
B
B
send
light_mode
delete
Question #33
Which option is an advantage to using network-based anti-virus versus host-based anti-virus?
- ANetwork-based has the ability to protect unmanaged devices and unsupported operating systems.
- BThere are no advantages compared to host-based antivirus.
- CHost-based antivirus does not have the ability to collect newly created signatures.
- DNetwork-based can protect against infection from malicious files at rest.
Correct Answer:
A
A
send
light_mode
delete
Question #34
Which concern is important when monitoring NTP servers for abnormal levels of traffic?
- ABeing the cause of a distributed reflection denial of service attack.
- BUsers changing the time settings on their systems.
- CA critical server may not have the correct time synchronized.
- DWatching for rogue devices that have been added to the network.
Correct Answer:
A
A
send
light_mode
delete
Question #35
While viewing packet capture data, you notice that one IP is sending and receiving traffic for multiple devices by modifying the IP header. Which option is making this behavior possible?
send
light_mode
delete
Question #36
Which hashing algorithm is the least secure?
send
light_mode
delete
Question #37
You must create a vulnerability management framework. Which main purpose of this framework is true?
- AConduct vulnerability scans on the network.
- BManage a list of reported vulnerabilities.
- CIdentify, remove, and mitigate system vulnerabilities.
- DDetect and remove vulnerabilities in source code.
Correct Answer:
C
C
send
light_mode
delete
Question #38
Which definition of Windows Registry is true?
- Aset of pages that are currently resident in physical memory
- Bbasic unit to which the operating system allocates processor time
- Cset of virtual memory addresses
- Ddatabase that stores low-level settings for the operating system
Correct Answer:
D
D
send
light_mode
delete
Question #39
Which two features must a next generation firewall include? (Choose two.)
- Adata mining
- Bhost-based antivirus
- Capplication visibility and control
- DSecurity Information and Event Management
- Eintrusion detection system
Correct Answer:
CE
CE
send
light_mode
delete
Question #40
Which type of exploit normally requires the culprit to have prior access to the target system?
- Alocal exploit
- Bdenial of service
- Csystem vulnerability
- Dremote exploit
Correct Answer:
A
A
send
light_mode
delete
All Pages