Checkpoint 156-315.80 Exam Practice Questions (P. 5)
- Full Access (479 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #41
What happen when IPS profile is set in Detect Only Mode for troubleshooting?
- AIt will generate Geo-Protection traffic
- BAutomatically uploads debugging logs to Check Point Support Center
- CIt will not block malicious traffic
- DBypass licenses requirement for Geo-Protection control
Correct Answer:
C
It is recommended to enable Detect-Only for Troubleshooting on the profile during the initial installation of IPS. This option overrides any protections that are set to
Prevent so that they will not block any traffic.
During this time you can analyze the alerts that IPS generates to see how IPS will handle network traffic, while avoiding any impact on the flow of traffic.
Reference:
https://sc1.checkpoint.com/documents/R76/CP_R76_IPS_AdminGuide/12750.htm
C
It is recommended to enable Detect-Only for Troubleshooting on the profile during the initial installation of IPS. This option overrides any protections that are set to
Prevent so that they will not block any traffic.
During this time you can analyze the alerts that IPS generates to see how IPS will handle network traffic, while avoiding any impact on the flow of traffic.
Reference:
https://sc1.checkpoint.com/documents/R76/CP_R76_IPS_AdminGuide/12750.htm
send
light_mode
delete
Question #42
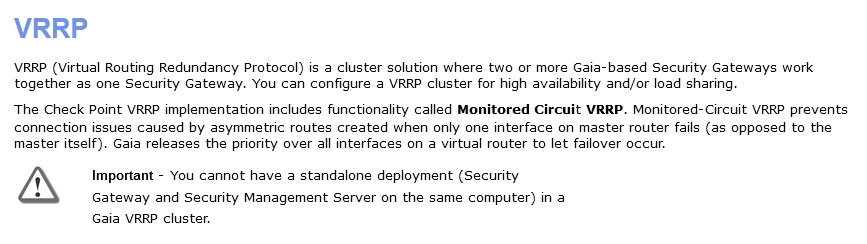
What is true about VRRP implementations?
- AVRRP membership is enabled in cpconfig
- BVRRP can be used together with ClusterXL, but with degraded performance
- CYou cannot have a standalone deployment
- DYou cannot have different VRIDs in the same physical network
Correct Answer:
C
Reference:
https://sc1.checkpoint.com/documents/R76/CP_R76_Gaia_WebAdmin/87911.htm
C
Reference:
https://sc1.checkpoint.com/documents/R76/CP_R76_Gaia_WebAdmin/87911.htm

send
light_mode
delete
Question #43
The Security Gateway is installed on GAIA R80. The default port for the Web User Interface is ______.
send
light_mode
delete
Question #44
Fill in the blank: The R80 feature ______ permits blocking specific IP addresses for a specified time period.
- ABlock Port Overflow
- BLocal Interface Spoofing
- CSuspicious Activity Monitoring
- DAdaptive Threat Prevention
Correct Answer:
C
Suspicious Activity Rules Solution
Suspicious Activity Rules is a utility integrated into SmartView Monitor that is used to modify access privileges upon detection of any suspicious network activity
(for example, several attempts to gain unauthorized access).
The detection of suspicious activity is based on the creation of Suspicious Activity rules. Suspicious Activity rules are Firewall rules that enable the system administrator to instantly block suspicious connections that are not restricted by the currently enforced security policy. These rules, once set (usually with an expiration date), can be applied immediately without the need to perform an Install Policy operation.
Reference:
https://sc1.checkpoint.com/documents/R76/CP_R76_SmartViewMonitor_AdminGuide/17670.htm
C
Suspicious Activity Rules Solution
Suspicious Activity Rules is a utility integrated into SmartView Monitor that is used to modify access privileges upon detection of any suspicious network activity
(for example, several attempts to gain unauthorized access).
The detection of suspicious activity is based on the creation of Suspicious Activity rules. Suspicious Activity rules are Firewall rules that enable the system administrator to instantly block suspicious connections that are not restricted by the currently enforced security policy. These rules, once set (usually with an expiration date), can be applied immediately without the need to perform an Install Policy operation.
Reference:
https://sc1.checkpoint.com/documents/R76/CP_R76_SmartViewMonitor_AdminGuide/17670.htm
send
light_mode
delete
Question #45
What is the mechanism behind Threat Extraction?
- AThis a new mechanism which extracts malicious files from a document to use it as a counter-attack against its sender.
- BThis is a new mechanism which is able to collect malicious files out of any kind of file types to destroy it prior to sending it to the intended recipient.
- CThis is a new mechanism to identify the IP address of the sender of malicious codes and put it into the SAM database (Suspicious Activity Monitoring).
- DAny active contents of a document, such as JavaScripts, macros and links will be removed from the document and forwarded to the intended recipient, which makes this solution very fast.
Correct Answer:
D
D
send
light_mode
delete
Question #46
You want to gather and analyze threats to your mobile device. It has to be a lightweight app. Which application would you use?
- ASmartEvent Client Info
- BSecuRemote
- CCheck Point Protect
- DCheck Point Capsule Cloud
Correct Answer:
C
C
send
light_mode
delete
Question #47
Which view is NOT a valid CPVIEW view?
send
light_mode
delete
Question #48
Which of the following is a new R80.10 Gateway feature that had not been available in R77.X and older?
- AThe rule base can be built of layers, each containing a set of the security rules. Layers are inspected in the order in which they are defined, allowing control over the rule base flow and which security functionalities take precedence.
- BLimits the upload and download throughput for streaming media in the company to 1 Gbps.
- CTime object to a rule to make the rule active only during specified times.
- DSub Policies ae sets of rules that can be created and attached to specific rules. If the rule is matched, inspection will continue in the sub policy attached to it rather than in the next rule.
Correct Answer:
D
Reference:
http://dl3.checkpoint.com/paid/1f/1f850d1640792cf885336cc6ae8b2743/CP_R80_ReleaseNotes.pdf?
HashKey=1517092603_dd917544d92dccc060e5b25d28a46f79&xtn=.pdf
D
Reference:
http://dl3.checkpoint.com/paid/1f/1f850d1640792cf885336cc6ae8b2743/CP_R80_ReleaseNotes.pdf?
HashKey=1517092603_dd917544d92dccc060e5b25d28a46f79&xtn=.pdf
send
light_mode
delete
Question #49
fwssd is a child process of which of the following Check Point daemons?
send
light_mode
delete
Question #50
Sticky Decision Function (SDF) is required to prevent which of the following? Assume you set up an Active-Active cluster.
send
light_mode
delete
All Pages
