CIW 1D0-571 Exam Practice Questions (P. 5)
- Full Access (62 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #21
Consider the following series of commands from a Linux system: iptables -A input -p icmp -s 0/0 -d 0/0 -j REJECT Which explanation best describes the impact of the resulting firewall ruleset?
- AIndividuals on remote networks will no longer be able to use SSH to control internal network resources.
- BInternal hosts will not be able to ping each other using ICMP.
- CStateful multi-layer inspection has been enabled.
- DIndividuals on remote networks will not be able to use ping to troubleshoot connections.
Correct Answer:
D
D
send
light_mode
delete
Question #22
A CGI application on the company's Web server has a bug written into it. This particular bug allows the application to write data into an area of memory that has not been properly allocated to the application. An attacker has created an application that takes advantage of this bug to obtain credit card information. Which of the following security threats is the attacker exploiting, and what can be done to solve the problem?
- A- Buffer overflow - Work with the Web developer to solve the problem
- B- SQL injection - Work with a database administrator to solve the problem
- C- Denial of service - Contact the organization that wrote the code for the Web server
- D- Man-in-the-middle attack
Correct Answer:
A
A
send
light_mode
delete
Question #23
A new server has been placed on the network. You have been assigned to protect this server using a packet-filtering firewall. To comply with this request, you have enabled the following ruleset:
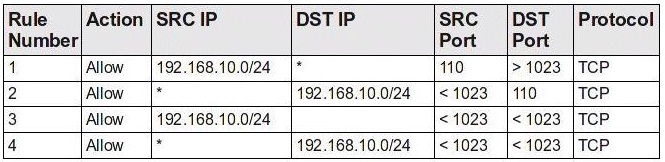
Which choice describes the next step to take now that this ruleset has been enabled?

Which choice describes the next step to take now that this ruleset has been enabled?
- AFrom the internal network, use your Web browser to determine whether all internal users can access the Web server.
- BFrom the internal network, use your e-mail client to determine whether all internal users can access the e-mail server.
- CFrom the external network, use your Web browser to determine whether all external users can access the Web server.
- DFrom the external network, use your e-mail client to determine whether all external users can access the e-mail server.
Correct Answer:
D
D
send
light_mode
delete
Question #24
The most popular types of proxy-oriented firewalls operate at which layer of the OSI/RM?
send
light_mode
delete
Question #25
You are using a PKI solution that is based on Secure Sockets Layer (SSL). Which of the following describes the function of the asymmetric-key-encryption algorithm used?
- AIt encrypts the symmetric key.
- BIt encrypts all of the data.
- CIt encrypts the hash code used for data integrity.
- DIt encrypts the X.509 key.
Correct Answer:
A
A
send
light_mode
delete
All Pages
