EC-Council 312-50v12 Exam Practice Questions (P. 1)
- Full Access (317 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #1
In this form of encryption algorithm, every individual block contains 64-bit data, and three keys are used, where each key consists of 56 bits. Which is this encryption algorithm?
- AIDEA
- BTriple Data Encryption StandardMost Voted
- CAES
- DMD5 encryption algorithm
Correct Answer:
B
B
 GPT-4o - Answer
GPT-4o - Answer
Triple Data Encryption Standard (Triple DES) uses a 64-bit data block along with three separate keys, each being 56 bits in length. This encryption method applies the DES algorithm three times to every data block, thereby enhancing the encryption security compared to single DES. Remember, when you see references to 64-bit blocks and three 56-bit keys, you’re definitely looking at Triple DES. Make sure this fundamental is clear as you prep for the exam!
send
light_mode
delete
Question #2
John is investigating web-application firewall logs and observers that someone is attempting to inject the following:
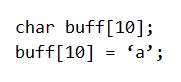
What type of attack is this?
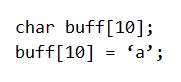
What type of attack is this?
send
light_mode
delete
Question #3
John, a professional hacker, performs a network attack on a renowned organization and gains unauthorized access to the target network. He remains in the network without being detected for a long time and obtains sensitive information without sabotaging the organization.
Which of the following attack techniques is used by John?
Which of the following attack techniques is used by John?
- AInsider threat
- BDiversion theft
- CSpear-phishing sites
- DAdvanced persistent threatMost Voted
Correct Answer:
D
D
 GPT-4o - Answer
GPT-4o - Answer
The correct choice, "D) Advanced persistent threat," is affirmed by the scenario in which John remains undetected in the network for a prolonged period while accessing sensitive information. This characteristic of stealth and persistence without disruption fits the profile of an APT, where the emphasis is on long-term access that allows an attacker to continuously gather data without being discovered, differentiating it sharply from other, more immediate and disruptive forms of cyberattacks.
send
light_mode
delete
Question #4
You are attempting to run an Nmap port scan on a web server. Which of the following commands would result in a scan of common ports with the least amount of noise in order to evade IDS?
- Anmap -A - Pn
- Bnmap -sP -p-65535 -T5
- Cnmap -sT -O -T0Most Voted
- Dnmap -A --host-timeout 99 -T1
Correct Answer:
C
C
 GPT-4o - Answer
GPT-4o - Answer
Option C, which uses the flags -sT -O -T0, is the most suitable for scanning with minimal noise. The -T0 flag, often referred to as "paranoid," slows down the scan significantly. This slow speed is strategic, allowing the scan to operate under the radar of most Intrusion Detection Systems (IDS), thus minimizing the chances of detection. While this makes the scan much slower, it is the best approach when stealth is more important than speed, making it ideal for sensitive environments where avoiding detection is critical. This setting aligns with established best practices for conducting discreet network scans.
send
light_mode
delete
Question #5
This wireless security protocol allows 192-bit minimum-strength security protocols and cryptographic tools to protect sensitive data, such as GCMP-256, HMAC-SHA384, and ECDSA using a 384-bit elliptic curve.
Which is this wireless security protocol?
Which is this wireless security protocol?
- AWPA3-Personal
- BWPA3-EnterpriseMost Voted
- CWPA2-Enterprise
- DWPA2-Personal
Correct Answer:
B
B
 GPT-4o - Answer
GPT-4o - Answer
WPA3-Enterprise is tailored for environments demanding robust security, like enterprise settings. It employs advanced 192-bit security protocols, such as GCMP-256, and cryptographic tools, including HMAC-SHA384 and ECDSA with a 384-bit curve. This significant security uplift over earlier versions effectively shields against various sophisticated attacks, securing sensitive data in large-scale networks.
send
light_mode
delete
Question #6
What are common files on a web server that can be misconfigured and provide useful information for a hacker such as verbose error messages?
- Ahttpd.conf
- Badministration.config
- Cphp.iniMost Voted
- Didq.dll
Correct Answer:
C
C
 GPT-4o - Answer
GPT-4o - Answer
The php.ini file plays a critical role in the configuration of PHP on servers. Misconfiguration of this file can indeed lead to verbose error messages which inadvertently provide detailed insights into the server's operations. These insights can be exploited by a hacker to gather more information about the server and potentially find vulnerabilities. Recognizing and securing such configurations is essential for maintaining robust server security. It's mentioned as a source of verbose error messages in these settings, underscoring the importance of correct configuration practices.
send
light_mode
delete
Question #7
Gerard, a disgruntled ex-employee of Sunglass IT Solutions, targets this organization to perform sophisticated attacks and bring down its reputation in the market. To launch the attacks process, he performed DNS footprinting to gather information about DNS servers and to identify the hosts connected in the target network. He used an automated tool that can retrieve information about DNS zone data including DNS domain names, computer names, IP addresses, DNS records, and network Whois records. He further exploited this information to launch other sophisticated attacks.
What is the tool employed by Gerard in the above scenario?
What is the tool employed by Gerard in the above scenario?
- ATowelroot
- BKnative
- CzANTI
- DBlutoMost Voted
Correct Answer:
D
D
 GPT-4o - Answer
GPT-4o - Answer
Bluto is indeed the appropriate tool Gerard used, as it specializes in DNS footprinting. This tool efficiently gathers crucial DNS zone data such as domain names, computer names, IP addresses, and network Whois records. By automating the information retrieval process, it speeds up the attack preparation phase, allowing a hacker like Gerard to comprehensively map out the target network and plan sophisticated subsequent attacks. This capability makes Bluto invaluable for someone looking to exploit network vulnerabilities found in DNS data to compromise security further.
send
light_mode
delete
Question #8
Tony is a penetration tester tasked with performing a penetration test. After gaining initial access to a target system, he finds a list of hashed passwords.
Which of the following tools would not be useful for cracking the hashed passwords?
Which of the following tools would not be useful for cracking the hashed passwords?
- AHashcat
- BJohn the Ripper
- CTHC-Hydra
- DnetcatMost Voted
Correct Answer:
B
B
 GPT-4o - Answer
GPT-4o - Answer
Absolutely, the correct answer should indeed be D, netcat. The tool is primarily used for network communications and isn't designed to handle password cracking tasks like Hashcat or John the Ripper. It's great for different backend activities and some neat network tricks, but when it comes to cracking hashed passwords, it's just not going to cut it. Always handy to remember what each tool is really made for!
send
light_mode
delete
Question #9
Which of the following Google advanced search operators helps an attacker in gathering information about websites that are similar to a specified target URL?
- A[inurl:]
- B[info:]
- C[site:]
- D[related:]Most Voted
Correct Answer:
D
D
 GPT-4o - Answer
GPT-4o - Answer
The correct answer is D: [related:]. This Google advanced search operator is crucial for identifying websites similar to the one specified. For ethical hackers, this tool is particularly useful as it helps to discover potential linked systems that could harbor similar vulnerabilities or be part of a larger network associated with the primary target. Understanding the usage of the [related:] operator enhances the breadth of a preemptive security assessment, thereby contributing significantly to comprehensive vulnerability analysis.
send
light_mode
delete
Question #10
You are a penetration tester working to test the user awareness of the employees of the client XYZ. You harvested two employees’ emails from some public sources and are creating a client-side backdoor to send it to the employees via email.
Which stage of the cyber kill chain are you at?
Which stage of the cyber kill chain are you at?
- AReconnaissance
- BWeaponizationMost Voted
- CCommand and control
- DExploitation
Correct Answer:
D
D
 GPT-4o - Answer
GPT-4o - Answer
Actually, the correct phase is weaponization, not exploitation. During this stage, you're engaged in creating and preparing the malicious payload - here, the client-side backdoor - which you'll later send (deliver) to the targeted employees. This preparation directly aligns with the definition of weaponization in the cyber kill chain framework, involving the development of tools designed to exploit vulnerabilities identified in the reconnaissance phase.
send
light_mode
delete
All Pages
