Oracle 1z0-897 Exam Practice Questions (P. 1)
- Full Access (120 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #1
An airline built and deployed a back-end application to manage reservations. To support interoperability with as large a base of standalone client applications as possible, the services provided by this back-end application are exposed as XML-based restful web services. Management just added a new requirement that
AJAX-based web application clients be supported, too. One of the developers suggested that it is enough to extend the existing application to support both XML- based and JSON-based restful web services. Assuming the developer is correct, choose the sentence that best describes an attempt to introduce this ability as this developer suggests (Choose one):
AJAX-based web application clients be supported, too. One of the developers suggested that it is enough to extend the existing application to support both XML- based and JSON-based restful web services. Assuming the developer is correct, choose the sentence that best describes an attempt to introduce this ability as this developer suggests (Choose one):
- AThe attempt will fail, because JAX-RS does not support both XML- and JSON- based restful services in parallel.
- BThe attempt will be trivial to implement, since JAX-RS just needs for the application to specify that both XML- and JSON-based interaction will be supported.
- CThe attempt can succeed, but it will require a significant amount of new code, since JAX-RS does support both XML- and JSON-based interaction - but not single resource can support both kinds of interaction simultaneously.
- DThe attempt will fail, because there is more to the difference between XML-based and JSON-based interactions than just the data representation used.
Correct Answer:
B
B
send
light_mode
delete
Question #2
A company is refactoring an existing website to use Web services clients. The application retrieves lists of parts and displays them to the users in a browser window. Previously, the data was stored as files on the web server and, in order to access the files, the user would simply click on a hyperlink. Now the data must be dynamically generated via a service that another developer has created. They want the easiest way to refactor their website to use Web services. Which three client-side technologies should they use? (Choose three.)
send
light_mode
delete
Question #3
In the code fragment below, the client will use os to upload data to the web service provider.
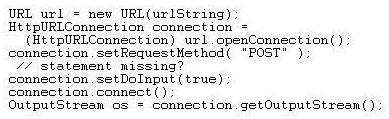
Choose the statement that must be placed in line 5, to ensure this fragment works as intended. (Choose one)

Choose the statement that must be placed in line 5, to ensure this fragment works as intended. (Choose one)
- Aconnection.setDoOutput(true);
- Bconnection.setAllowUserInteraction(true);
- Cconnection.setIfModifiedSince(new Date().getTime());
- Dconnection.setUseCaches(false);
Correct Answer:
A
A
send
light_mode
delete
Question #4
Given the resource class fragment:
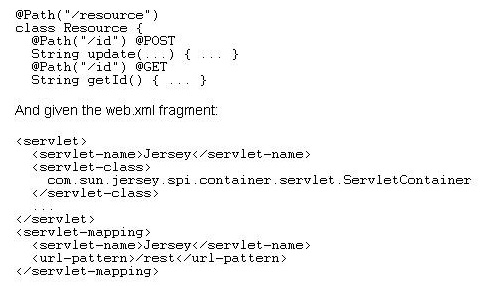
Choose the code fragment below that would secure access only to the Resource update() method (Choose one):

Choose the code fragment below that would secure access only to the Resource update() method (Choose one):
- A<security-constraint> <web-resource-collection> <url-pattern>/rest</url-pattern> <http-method>GET</http-method> <http-method>POST</http-method> </web-resource-collection>
- B<security-constraint> <web-resource-collection> <url-pattern>/rest</url-pattern> <http-method>POST</http-method> </web-resource-collection>
- C<security-constraint> <web-resource-collection> <url-pattern>/rest/id</url-pattern> <http-method>POST</http-method> <http-method>GET</http-method> </web-resource-collection>
- D<security-constraint>D.<security-constraint> <web-resource-collection> <url-pattern>/id</url-pattern> <http-method>POST</http-method>
Correct Answer:
B
B
send
light_mode
delete
Question #5
An organization has business logic implemented in EJB components. Current clients use container-managed, role-based security to access the business logic using RMI. Management has determined that the business logic must be made available to non-RMI clients using a Web service. Which container-managed Web service security mechanism would the development team?use to allow Web service clients to use the current security model? (Choose one)
- AXKMS
- BXACML
- CXML Digital Signature
- DHTTP Basic Authentication
- Eannotations mapped to the JAX-WS runtime
Correct Answer:
D
D
send
light_mode
delete
All Pages
