CompTIA CAS-005 Exam Practice Questions (P. 1)
- Full Access (408 questions)
- One Year of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #1
A security engineer is reviewing event logs because an employee successfully connected a personal Windows laptop to the corporate network, which is against company policy. Company policy allows all Windows 10 and 11 laptops to connect to the system as long as the MDM agent installed by IT is running. Only compliant devices can connect, and the logic in the system to evaluate compliant laptops is as follows:
Which of the following most likely occurred when the employee connected a personally owned Windows laptop and was allowed on the network?
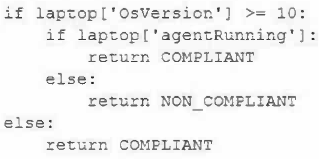
Which of the following most likely occurred when the employee connected a personally owned Windows laptop and was allowed on the network?

- AThe agent was not running on the laptop, which triggered a false positive.
- BThe OS was a valid version, but the MDM agent was not installed, triggering a true positive.
- CThe OS was running a Windows version below 10 and triggered a false negative.
- DThe OS version was higher than 11, and the MDM agent was running, triggering a true negative.
send
light_mode
delete
Question #2
An organization is working to secure its development process to ensure developers cannot deploy artifacts directly into the production environment. Which of the following security practice recommendations would be the best to accomplish this objective?
- AImplement least privilege access to all systems.
- BRoll out security awareness training for all users.
- CSet up policies and systems with separation of duties.
- DEnforce job rotations for all developers and administrators.
- EUtilize mandatory vacations for all developers.
- FReview all access to production systems on a quarterly basis.
send
light_mode
delete
Question #3
A security architect discovers the following while reviewing code for a company's website: selection = "SELECT Item FROM Catalog WHERE ItemID = " & Request("ItemID")
Which of the following should the security architect recommend?
Which of the following should the security architect recommend?
- AClient-side processing
- BQuery parameterization
- CData normalization
- DEscape character blocking
- EURL encoding
send
light_mode
delete
Question #4
A security architect needs to enable a container orchestrator for DevSecOps and SOAR initiatives. The engineer has discovered that several Ansible YAML files used for the automation of configuration management have the following content:
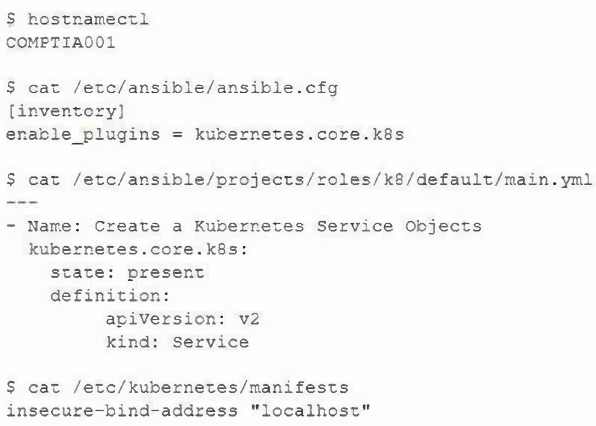
Which of the following should the engineer do to correct the security issues presented within this content?

Which of the following should the engineer do to correct the security issues presented within this content?
- AUpdate the kubernetes.core.k8s module to kubernetes.core.k8s_service in the main.yml file.
- BUpdate the COMPTIA001 hostname to localhost using the hostnamectl command.
- CUpdate the state: present module to state: absent in the main.yml file.
- DUpdate or remove the ansible.cfg file.
- EUpdate the insecure-bind-address from localhost to the COMPTIA001 in the manifests file.
send
light_mode
delete
Question #5
A CRM company leverages a CSP PaaS service to host and publish Its SaaS product. Recently, a large customer requested that all infrastructure components must meet strict regulatory requirements, including configuration management, patch management, and life-cycle management. Which of the following organizations is responsible for ensuring those regulatory requirements are met?
- AThe CRM company
- BThe CRM company's customer
- CThe CSP
- DThe regulatory body
send
light_mode
delete
Question #6
Company A is merging with Company B. Company A is a small, local company. Company B has a large, global presence. The two companies have a lot of duplication in their IT systems, processes, and procedures. On the new Chief Information Officer's (CIO's) first day, a fire breaks out at Company B's main data center. Which of the following actions should the CIO take first?
- ADetermine whether the incident response plan has been tested at both companies, and use it to respond.
- BReview the incident response plans, and engage the disaster recovery plan while relying on the IT leaders from both companies.
- CEnsure hot, warm, and mobile disaster recovery sites are available, and give an update to the companies' leadership teams.
- DInitiate Company A's IT systems processes and procedures, assess the damage, and perform a BIA.
send
light_mode
delete
Question #7
The results of an internal audit indicate several employees reused passwords that were previously included in a published list of compromised passwords.
The company has the following employee password policy:
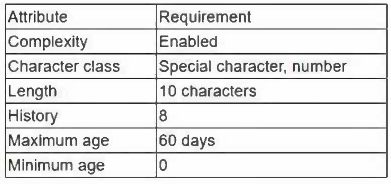
Which of the following should be implemented to best address the password reuse issue? (Choose two.)
The company has the following employee password policy:

Which of the following should be implemented to best address the password reuse issue? (Choose two.)
- AIncrease the minimum age to two days.
- BIncrease the history to 20.
- CIncrease the character length to 12.
- DAdd case-sensitive requirements to character class.
- EDecrease the maximum age to 30 days.
- FRemove the complexity requirements.
- GIncrease the maximum age to 120 days.
send
light_mode
delete
Question #8
A mobile administrator is reviewing the following mobile device DHCP logs to ensure the proper mobile settings are applied to managed devices:
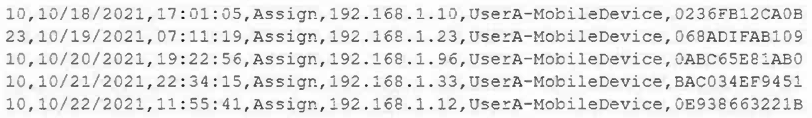
Which of the following mobile configuration settings is the mobile administrator verifying?

Which of the following mobile configuration settings is the mobile administrator verifying?
- AService set identifier authentication
- BWireless network auto joining
- C802.1X with mutual authentication
- DAssociation MAC address randomization
send
light_mode
delete
Question #9
A security analyst is investigating a possible insider threat incident that involves the use of an unauthorized USB from a shared account to exfiltrate data. The event did not create an alert. The analyst has confirmed the USB hardware ID is not on the device allow list, but has not yet confirmed the owner of the USB device. Which of the following actions should the analyst take next?
- AClassify the incident as a false positive.
- BClassify the incident as a false negative.
- CClassify the incident as a true positive.
- DClassify the incident as a true negative.
send
light_mode
delete
Question #10
Which of the following security features do email signatures provide?
- ANon-repudiation
- BBody encryption
- CCode signing
- DSender authentication
- EChain of custody
send
light_mode
delete
All Pages
