Cisco® 300-730 Exam Practice Questions (P. 1)
- Full Access (224 questions)
- Six months of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #1
DRAG DROP -
Drag and drop the correct commands from the right onto the blanks within the code on the left to implement a design that allow for dynamic spoke-to-spoke communication. Not all commands are used.
Select and Place:
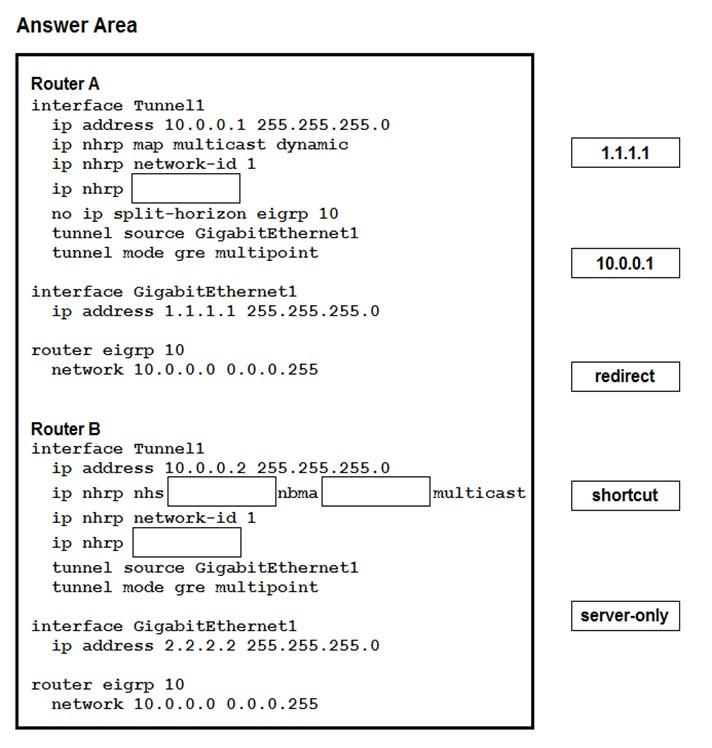
Drag and drop the correct commands from the right onto the blanks within the code on the left to implement a design that allow for dynamic spoke-to-spoke communication. Not all commands are used.
Select and Place:

Correct Answer:
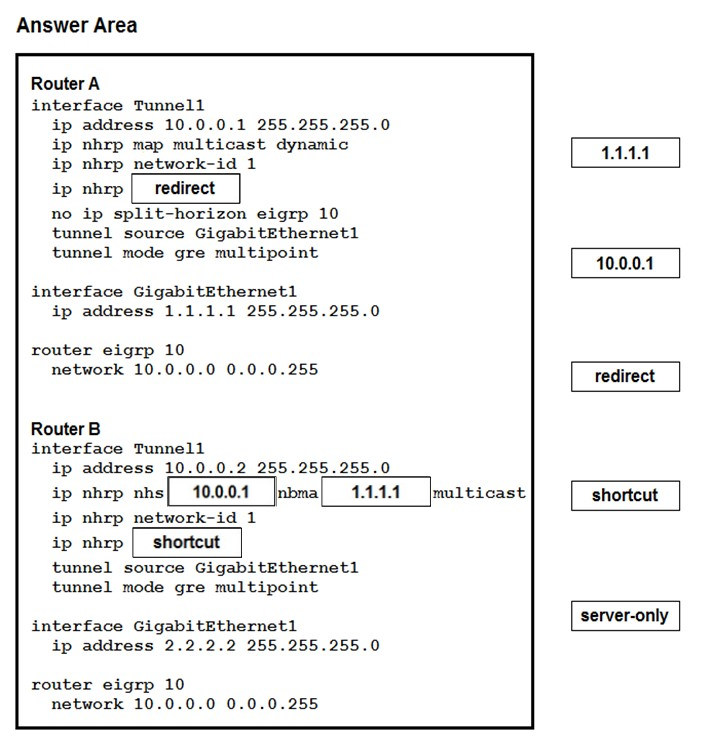
Reference:
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_conn_dmvpn/configuration/xe-16/sec-conn-dmvpn-xe-16-book/sec-conn-dmvpn-summ- maps.html

Reference:
https://www.cisco.com/c/en/us/td/docs/ios-xml/ios/sec_conn_dmvpn/configuration/xe-16/sec-conn-dmvpn-xe-16-book/sec-conn-dmvpn-summ- maps.html
send
light_mode
delete
Question #2
A second set of traffic selectors is negotiated between two peers using IKEv2. Which IKEv2 packet will contain details of the exchange?
- AIKEv2 IKE_SA_INIT
- BIKEv2 INFORMATIONAL
- CIKEv2 CREATE_CHILD_SAMost Voted
- DIKEv2 IKE_AUTH
Correct Answer:
B
B
 GPT-4o - Answer
GPT-4o - Answer
The IKEv2 CREATE_CHILD_SA packet is indeed the correct choice when it comes to negotiating a second set of traffic selectors between two peers. This exchange is used not only for rekeying the existing Child SAs but also for establishing new ones, which involves negotiating new traffic selectors. During the CREATE_CHILD_SA exchange, payloads such as the SA proposal and traffic selector proposal are essential, as they provide details about the traffic selectors like IP addresses and port numbers for the new or rekeyed Child SA. This makes the CREATE_CHILD_SA exchange crucial for dynamically managing security associations and traffic selectors in an IKEv2 VPN.
send
light_mode
delete
Question #3
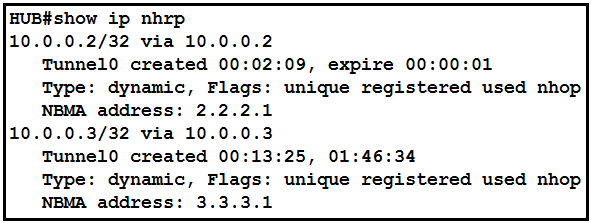
Refer to the exhibit. The DMVPN tunnel is dropping randomly and no tunnel protection is configured. Which spoke configuration mitigates tunnel drops?
A.
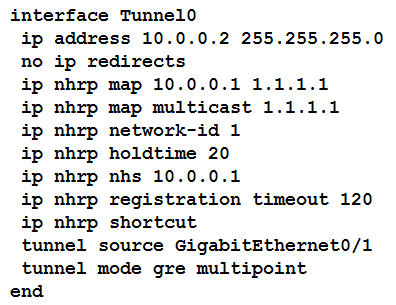
B.
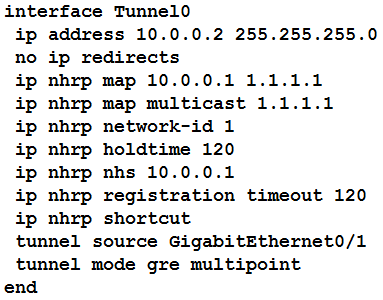
C.
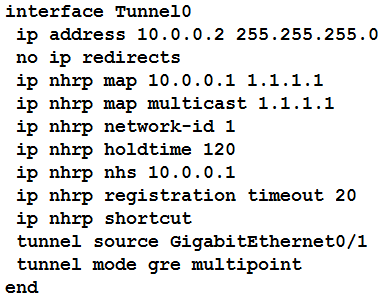
D.
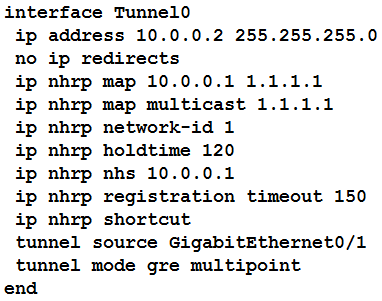
send
light_mode
delete
Question #4
On a FlexVPN hub-and-spoke topology where spoke-to-spoke tunnels are not allowed, which command is needed for the hub to be able to terminate FlexVPN tunnels?
- Ainterface virtual-access
- Bip nhrp redirect
- Cinterface tunnel
- Dinterface virtual-templateMost Voted
Correct Answer:
D
D
 GPT-4o - Answer
GPT-4o - Answer
The correct command for a FlexVPN hub in a hub-and-spoke topology where spoke-to-spoke communication is disallowed is "interface virtual-template". This command allows the hub to dynamically create virtual access interfaces necessary for each spoke connection. This setup avoids the necessity for fixed configurations per spoke, hence optimizing scalability and management of VPN connections. Additionally, any mention of "ip nhrp redirect" in this context is inappropriate because it's used for facilitating spoke-to-spoke communications, which are not desired in this scenario.
send
light_mode
delete
Question #5
Which statement about GETVPN is true?
- AThe configuration that defines which traffic to encrypt originates from the key server.Most Voted
- BTEK rekeys can be load-balanced between two key servers operating in COOP.
- CThe pseudotime that is used for replay checking is synchronized via NTP.
- DGroup members must acknowledge all KEK and TEK rekeys, regardless of configuration.
Correct Answer:
A
A
 GPT-4o - Answer
GPT-4o - Answer
In GETVPN, the key server plays a crucial role as it determines the traffic encryption policy for Group Members (GMs). By centralizing the encryption configuration, the key server enhances security management and operational efficiency across the network by specifying which traffic should be encrypted. This setup not only simplifies the administrative overhead but also strengthens security by maintaining consistent policy application among all group members.
send
light_mode
delete
All Pages
