Cisco® 300-725 Exam Practice Questions (P. 1)
- Full Access (60 questions)
- Six months of Premium Access
- Access to one million comments
- Seamless ChatGPT Integration
- Ability to download PDF files
- Anki Flashcard files for revision
- No Captcha & No AdSense
- Advanced Exam Configuration
Question #1
DRAG DROP -
Drag and drop the Cisco WSA methods from the left onto the correct deployment modes on the right.
Select and Place:
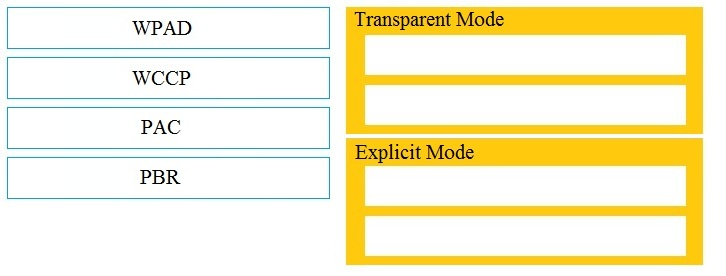
Drag and drop the Cisco WSA methods from the left onto the correct deployment modes on the right.
Select and Place:

Correct Answer:
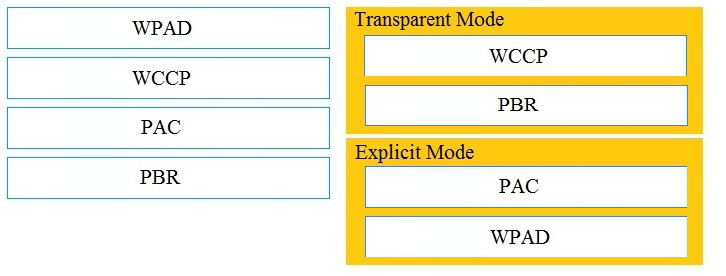
You could use an explicit setting (browser config/PAC/WPAD) or transparent (WCCP/PBR) to point to the first proxy and then the first proxy will route based on category to one of the two upstream proxies based on your policy configuration.
Reference:
https://community.cisco.com/t5/web-security/route-to-wsa-based-on-destination/td-p/2491179

You could use an explicit setting (browser config/PAC/WPAD) or transparent (WCCP/PBR) to point to the first proxy and then the first proxy will route based on category to one of the two upstream proxies based on your policy configuration.
Reference:
https://community.cisco.com/t5/web-security/route-to-wsa-based-on-destination/td-p/2491179
send
light_mode
delete
Question #2
What causes authentication failures on a Cisco WSA when LDAP is used for authentication?
- Awhen the passphrase contains only 5 characters
- Bwhen the passphrase contains characters that are not 7-bit ASCI
- Cwhen the passphrase contains one of following characters "˜@ # $ % ^'
- Dwhen the passphrase contains 50 characters
Correct Answer:
B
Reference:
https://www.cisco.com/c/en/us/td/docs/security/wsa/wsa11-0/user_guide/b_WSA_UserGuide/b_WSA_UserGuide_appendix_011001.html
B
Reference:
https://www.cisco.com/c/en/us/td/docs/security/wsa/wsa11-0/user_guide/b_WSA_UserGuide/b_WSA_UserGuide_appendix_011001.html
send
light_mode
delete
Question #3

Refer to the exhibit. Which statement about the transaction log is true?
- AThe log does not have a date and time
- BThe proxy had the content and did not contact other servers
- CThe transaction used TCP destination port 8187
- DThe AnalizeSuspectTraffic policy group was applied to the transaction
Correct Answer:
D
D
send
light_mode
delete
Question #4
Which two features can be used with an upstream and downstream Cisco WSA web proxy to have the upstream WSA identify users by their client IP address?
(Choose two.)
(Choose two.)
- AX-Forwarded-For
- Bhigh availability
- Cweb cache
- Dvia
- EIP spoofing
Correct Answer:
AD
Reference:
https://www.cisco.com/c/en/us/td/docs/security/wsa/wsa11-0/user_guide/b_WSA_UserGuide/b_WSA_UserGuide_chapter_0100.html
AD
Reference:
https://www.cisco.com/c/en/us/td/docs/security/wsa/wsa11-0/user_guide/b_WSA_UserGuide/b_WSA_UserGuide_chapter_0100.html
send
light_mode
delete
Question #5
DRAG DROP -
Drag and drop the properties from the left onto the correct advanced web proxy setting descriptions on the right.
Select and Place:
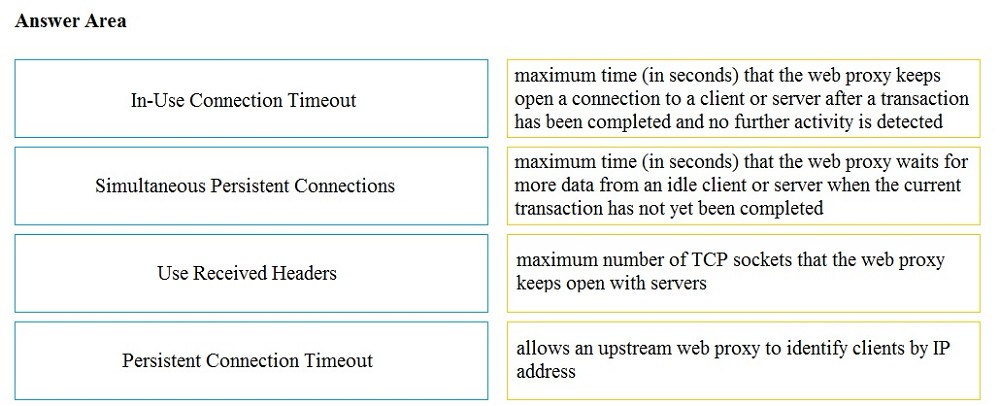
Drag and drop the properties from the left onto the correct advanced web proxy setting descriptions on the right.
Select and Place:

Correct Answer:
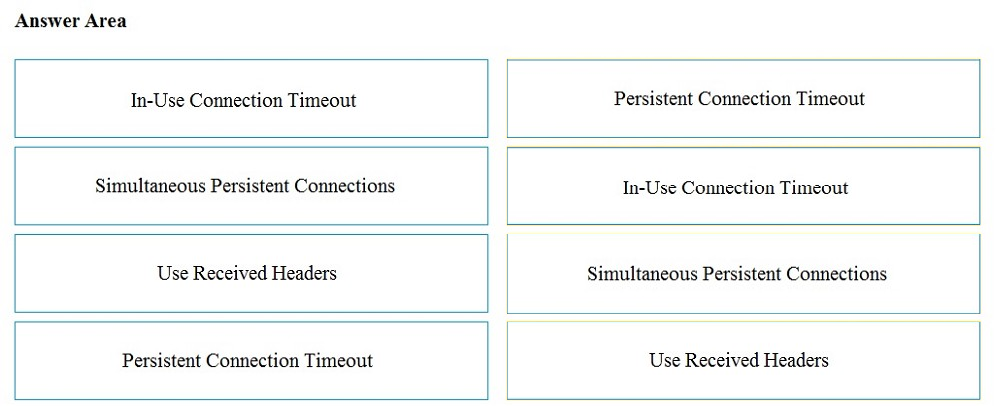
Reference:
https://www.cisco.com/c/en/us/td/docs/security/wsa/wsa11-0/user_guide/b_WSA_UserGuide/b_WSA_UserGuide_chapter_0100.html

Reference:
https://www.cisco.com/c/en/us/td/docs/security/wsa/wsa11-0/user_guide/b_WSA_UserGuide/b_WSA_UserGuide_chapter_0100.html
send
light_mode
delete
All Pages
